Paper Notes
Selected Paper Interpretation Notes.

Covers five major areas: database principles, framework tools, programming languages, algorithm analysis, and model analysis.
From database core principles to performance optimization practices, help developers build highly available data systems.
In-depth analysis of the core mechanisms of popular frameworks and tools such as Redis and Kafka, and release operation guides and best practices.
Focus on the underlying principles of languages such as Go/Python to improve code writing efficiency.
Systematically explain the implementation and application scenarios of classic algorithms such as Raft consensus algorithm, genetic algorithm, and Bloom filter.
Interpret the architecture design principles of machine learning models such as large models, combine mathematical derivation with engineering practice cases, and strengthen the algorithm implementation capabilities.
Focusing on paper interpretation, data mining and programming design, it helps developers advance their learning with systematic and in-depth content.
Selected top computer conference papers and authoritative works in the industry for reading and analysis.
In-depth interpretation of the seven core principles of object-oriented programming, combined with code examples to analyze the design logic of high cohesion and low coupling, provide practical demonstrations of scalable architecture, and help developers build easy-to-maintain and highly reusable software systems.
On the last day of 2025, I'm recording a RocketMQ message duplicate delivery issue I encountered this year. Essentially, it was caused by incorrect Consumer parameter settings.

In the actual development process, it is inevitable to create composite indexes for MySQL. However, considering the leftmost matching principle and some index failure scenarios, there are still some tricks to create indexes. This article will give some simple scenarios and discuss how to create MySQL composite indexes most effectively based on these scenarios.
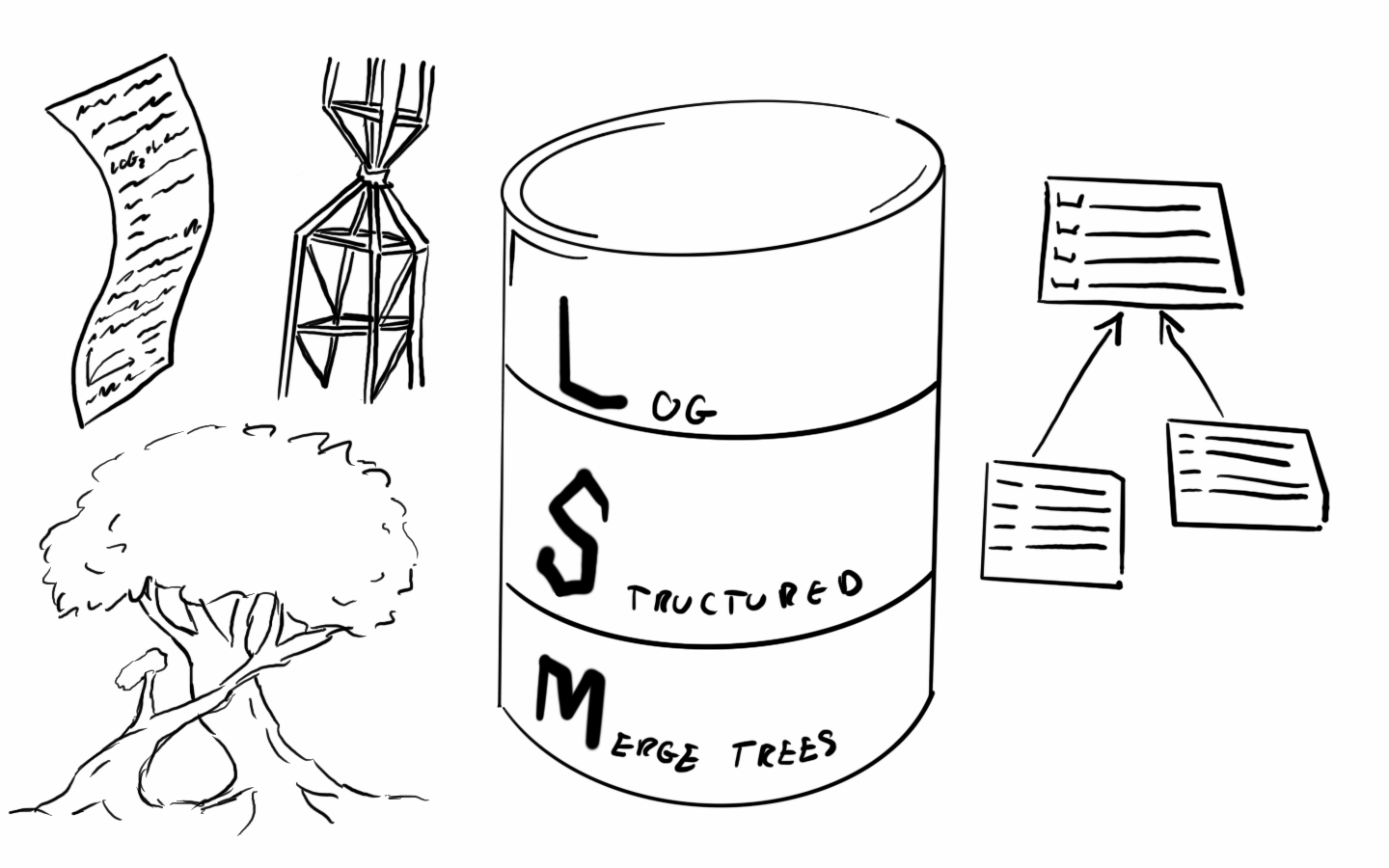
If you have ever been exposed to NoSQL databases, such as HBase, LevelDB, and RocksDB, then you should have heard of LSM trees. Most NoSQL databases have LSM trees at the bottom. The concept of LSM trees comes from a paper: The Log-Structured Merge-Tree ( LSM-Tree ). Today we will discuss the principles of LSM trees and how they add, delete, query, modify and merge data.

Almost all systems require users to register and log in, and the most common way to log in is to let users enter their username and password. Many early systems only required usernames and passwords to log in, but some websites have been attacked by brute force, social engineering refers to an attack method that manipulates human psychology rather than technical means to obtain passwords or sensitive information. The core is to exploit human weaknesses, such as trust, fear, curiosity or negligence, to induce the target to actively leak information or perform specific operations. refers to the data in the database being directly exported by the attacker.
This is a common scenario in e-commerce. Currently, Internet giants have very mature solutions for it. I wrote this article just to give some of my own thoughts.
MySQL, as a multi-threaded database, supports concurrent queries from clients and sets its default isolation level to repeatable read. So how does MySQL isolate transactions in concurrent operations? It actually uses the
If you are also a big data worker, you must have heard of the distributed file system:
With the development of the times, the application of foundation models in various fields is expanding. This article tries its best to sort out various materials and will give a brief overview of foundation models from the aspects of concept definition, type classification, training and application.
Redis is a very commonly used key-value database. The use of memory and HashMap for storage brings efficient queries. This article will introduce the persistence principle of Redis, the deployment method of clusters, and the expiration and elimination mechanism of key-value pairs.
Everything can be explained in one sentence.
ShenZhen, China
Dear readers,
Thank you for visiting my blog! I want to acknowledge that there aren't many posts in English here at the moment. As a native Chinese speaker, I've always written primarily in Chinese. However, I'm now working to translate my existing content into English to reach more readers.
This process involves using tools like Google Translate, so you may encounter occasional less-than-perfect expressions. I truly appreciate your understanding and patience as I navigate this transition.
The translation effort will take time, but I'm committed to bringing more content to you in English. Thank you for your support and for sticking around! 😄